24
Cybersecurity Risk Preparedness for Emerging Technologies
Cybersecurity risk preparedness is the practice of identifying potential risks and vulnerabilities, assessing the impacts and likelihood of those risks, and mitigating the consequences if the risks become reality. With today’s dynamic emerging educational technologies, the security landscape demands that every learning institution, no matter its size, develops and implements a cybersecurity risk preparedness plan. Investing time and resources in creating a cybersecurity risk preparedness plan illustrates that the institution recognizes that no one is immune to falling victim to a cyber-attack. A cybersecurity preparedness plan for emerging technologies requires that the school carries out a cybersecurity assessment and then develops a cybersecurity guideline that covers its needs comprehensively.
Cybersecurity assessments
1. Take stock of the school’s most valuable digital assets: The first thing to do is to identify the various assets that could be targeted by cybercriminals. These assets might include computers, systems, networks, or data. You will want to understand which of these assets criminals might want to target, which are most at risk of being targeted, and which might not be secure. If the thought of it being breached keeps you up at night, put it on your list.
2. Identify the risks, past and present: Once you have identified the assets you need to protect, you will need to identify the risks that could affect those assets. You will probably look at the risks associated with every threat that can affect your school, from unintentional ones like losing your mobile device to Ransomware attacks. Every potential threat, including new and emerging risks, should be identified.
You may also want to do a historical analysis of past cyber risks, attacks, and breaches, which will give you a window into your current risks. Any attack you have experienced in the past can offer you valuable information. In addition to giving you information about how attackers accessed your systems in the past, it will also shed light on the ways your team responded to those breaches at the time.
3. Plan for an attack: If a teacher or a student clicks a link and your school’s data is held to ransom, how will your institution respond? Part of mitigating risk is having a well-thought-out plan in advance. If you have to respond to an attack on the fly, you may not make the best decisions.
4. Review your controls: You may already have controls in place to prevent the risks you have identified or to respond to attacks if they occur. Review the controls you have in place to make sure they adequately cover your current risks. Continuous monitoring is important because the risk landscape is constantly changing and your controls should change to effectively protect your assets.
Creating a Cybersecurity Preparedness Plan
A cybersecurity preparedness plan is a series of events defining the best practices an organization follows to manage its cybersecurity risk. Such a plan reduces the company’s exposure to vulnerabilities. Every day, learning institutions of all sizes face the challenge of ensuring the security of their critical systems and data. To help address these challenges, a school needs a strategic, well-thought cybersecurity plan to protect its critical infrastructure and information systems.
There are several cybersecurity plans like the National Institute of Standards and Technology (NIST) and, ISO 27002. When applied properly, a cybersecurity plan enables IT, administrators, to manage their institution’s cyber risks more intelligently. A school can adapt an existing cybersecurity plan to meet its own needs or develop one internally.
Core components of a cybersecurity plan
Every cybersecurity plan is different. Thus, each describes core components in its own way. That said, they’re all built on similar principles, and they are used to achieve similar cybersecurity goals. While a specific cybersecurity plan goes into far greater detail in how it is constructed and designed, it loosely revolves around a continuous life-cycle process consisting of the following four key stages.
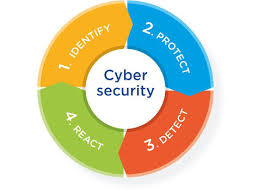
1. Identify and document cybersecurity goals. This component is used to identify the cybersecurity goals an educational institution wants to achieve. Identified goals will be different for each school. They are mostly dependent on the business’s level of cybersecurity competency, overall business intent, and whether the school must meet specific goals due to regulatory requirements.
2. Set guidelines designed to achieve cybersecurity goals. In this stage of a cybersecurity plan, a detailed list of functions, processes, and actions are created that serve to achieve the goals outlined in the identification stage. This stage should also contain steps to prioritize goals and define roles and responsibilities for each defined objective.
3. Implement cybersecurity processes. This is the action stage of the plan, where each goal is implemented within the school infrastructure. Communication is crucial in this stage as applied cybersecurity processes often involve multiple areas or departments.
4. Monitor and communicate results. Lastly, the implemented objectives are monitored, documented, and reviewed to ensure the cybersecurity plan processes are effective. Results are appropriately communicated to the school, and steps are taken to continuously improve existing processes and objectives.


