11

Data protection is the process of safeguarding important information from corruption, compromise or loss. It is approximated that each person in the world generates 1.7 MB of data every second. This data is a goldmine for hackers and thus needs to be protected as they can use it to perpetrate attacks or steal identities. Data protection employs various techniques to safeguard the confidentiality, integrity and availability of data. Due to large volumes of data, it is vital to classify data according to its sensitivity as this will determine the levels of security applied to each class of data. One of the most commonly used data protection techniques is encryption.
Encryption
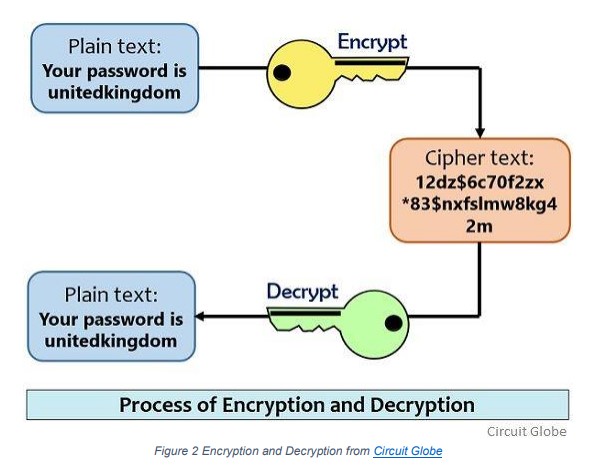
Encryption is a technique that allows information to be hidden so that it cannot be read without special knowledge, such as a password or a secret key. Encryption uses a secret key to change data into an unreadable or unintelligible format. The scrambled information is said to be encrypted and is known as ciphertext. Decryption is a way to convert encrypted data into a readable format or plaintext. Data that is stored or in transit should be encrypted to protect it from unauthorized access and modification, hence preserving its confidentiality and integrity. The figure below shows the encryption and decryption process. The user is sending confidential information about the password to a system. The message which is ‘Your password is unitedkingdom’ is encrypted into an unreadable format. A key is then used to convert the ciphertext into readable format once the data reaches its destination. Note that the password used in this example is weak and should not be used.
There are two popular solutions used to perform full drive/volume encryption; BitLocker and VeraCrypt.
BitLocker
BitLocker is a Microsoft proprietary encryption solution that is included with Microsoft Windows versions starting with Windows Vista. It protects the data on your device so it can only be accessed by people who have authorization. To turn BitLocker on, follow these steps:
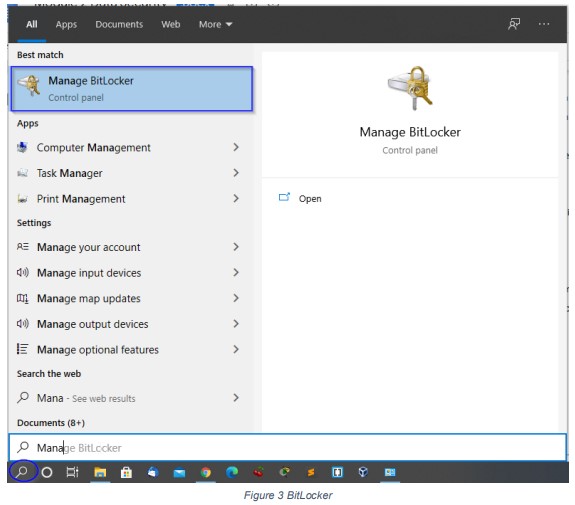
1. In the search box on the taskbar, type Manage BitLocker and then select it from the list of results as shown in Figure 3
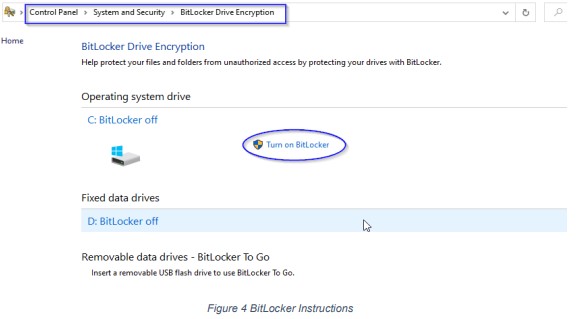
2. Click Turn on BitLocker then follow the instructions as shown in the figure below.
BitLocker also offers encryption of external drives such as USB drives. This solution is known as BitLocker To Go, and it protects the data stored in these external drives against tampering or unauthorized access. In case the drive is lost, the data will remain intact as someone would require the password used for encryption. This option is viable when sharing sensitive data with colleagues using external drives. To use this capability:
- Insert the USB drive or external drive to encrypt
- Search for Manage BitLocker using the search box on the taskbar
- Select BitLocker To Go and follow instructions. You’ll be prompted for your unlock method—for example, a password—when you connect the drive to your computer. If someone doesn’t have the unlock method, they can’t access the files on the drive.
- Back up the recovery key: After setting up BitLocker, it is crucial that the recovery key be backed up in case one forgets the password. This key can be backed up on an external drive such as USB drives. Avoid backing up the key to the cloud as cloud drives can be compromised.
VeraCrypt
VeraCrypt is a more sophisticated and robust encryption solution that enables full volume encryption, creation of hidden drives/folders and encryption of specific folders or files. Due to its robustness, VeraCrypt is recommended more than BitLocker. However, these two tools can be used together, BitLocker for full disk encryption at the push of a button, and VeraCrypt for specific folder encryption. To learn how to set up VeraCrypt, watch the video available at the link below.
Other than encryption, here are other guidelines and techniques that can be used to protect data:
- Back up sensitive data: Creating duplicates of files can ensure that if the device is lost, stolen, or compromised, you don’t also lose your important information. Backups can be created on the cloud. However, ensure the cloud service is secure.
- Remote location and device wiping: If your mobile phone or laptop has this feature, enable it. In case the device is lost or stolen, you can track it and delete all your information to prevent it from landing on the wrong hands.
- Lock your devices using passwords, PINs or fingerprint to prevent unauthorized access.
- Factory reset your devices before donating or reselling. This prevents the accidental leaking of data.
- Sharing personal data: Be overly cautious when sharing personal information, especially over the internet. Sharing too much information could make you a target for malicious attacks.
- Shred: Any old documents should be discarded through shredding. This prevents leaking of any personal information.
- Whenever possible, enable two-factor authentication. This will prevent access to email accounts and social media sites that have a sea of information about you.
- Avoid sharing any sensitive data over public WiFi as this data can be easily hijacked by attackers. For example, do not enter any credit card information on a website while using public WiFi.
- Always sign out from your accounts when using shared devices. This prevents other people from accessing data stored in your accounts.
- Separate personal data and work/professional data. Store this data separately. This will limit the extent of access an unauthorized person has in case you are compromised.
- Store most sensitive data locally. It is important to backup data in the cloud. However, your most sensitive data is most safe when stored in the devices you own. You can back up this data on encrypted external drives.