19
The internet, telecommunication networks, advancement in technology and ease of access to the internet have made communicating with people easier than ever, but as we’ve seen previously, it has also made surveillance more prevalent. The COVID pandemic has further accelerated wider adoption of online communication. Online communication in almost all sectors of the economy has become the norm and contextually, online learning has become something that both educators and learners have had to learn and adapt to over a very short period of time. Without taking extra steps to protect your privacy, every phone call, text message, email, instant message, video and audio chat, and social media message that you share with your students or colleagues could be vulnerable to eavesdroppers.
Often the most privacy-protective way to communicate with others is in person, without computers or phones being involved at all. Because this isn’t always possible, especially now, the next best thing is to use end-to-end encryption. We have looked at encryption in the video preceding this article and by now you have a clear understanding of how encryption works. So, how do we ensure that our communication, especially online is secure and encrypted? We’ll look at 3 major ways that we communicate online: via our mobile phones, over email and on other channels especially while teaching and learning.
Securing Mobile Communication
When you make a call from a landline or from your mobile phone, your call is not end-to-end encrypted, The same is true for text messages. This can allow governments, law enforcement, malicious actors or anyone else with the expertise to read your text messages or even record your phone calls. To ensure that no one can intercept your communication, you may prefer to use encrypted alternatives that operate over the Internet. As a bonus, many of these encrypted alternatives also offer video capabilities.
Some examples of services or software that offer end-to-end encrypted texting and voice and video calls include:
- Signal (for iOS and Android
- WhatsApp (for iOS and Android)
- Wire
Some examples of services that do not offer end-to-end encryption by default include:
- Google Hangouts
- Kakao Talk
- Line
- Snapchat
- Yahoo Messenger
And some services, like Facebook Messenger and Telegram, only offer end-to-end encryption if you deliberately turn it on. Others, like iMessage, only offer end-to-end encryption when both users are using a particular device (in the case of iMessage, both users need to be using an iPhone).
It is a good idea to do some research on whatever software you use to communicate digitally. Doing so will help you make appropriate choices based on your needs. Before choosing a chat application, it is important to consider the following:
- Is it end-to-end encrypted?
- Is it open-source? Open-source software means the code is published online, and freely available to be studied and commented on by anyone in
the world. The benefit of open-source technology is that if there is a security vulnerability in the code, there is a higher chance of someone catching it and speaking up about it, and that issue getting fixed quickly. - What does the company collect and store about you? The less a chat app collects about you, the less they can divulge about you.
- Do you have to connect your phone number to the app? While most chat apps require your phone number to sign up, there are a few privacy conscious chat apps that give you the option to create a username, rather than connect to your phone number. Wire is one such example.
With about 2 billion users, WhatsApp is one of the most commonly used channels of communication. So, what security features does it have and how can we ensure that WhatsApp is more secure and private?
- Turn on security notifications. When a new phone or laptop accesses an existing chat, a new security code is generated for both phones. And
WhatsApp can send a notification when the security code changes. This way, you can check the encryption with your friend over a different messenger, ensuring its security. To turn on security notifications, go to WhatsApp > Settings > Account > Security > Show security notifications and flip the toggle to green. - Enable two factor authentication if it is supported. 2FA adds a periodic passcode to WhatsApp, and also ensures that your data isn’t accessed by
someone else. This is perfect because unfortunately there’s no way to lock WhatsApp with a password, unless with a third party locking app on Android. Apple doesn’t allow locking WhatsApp with a passcode or Touch ID. To activate 2FA, go to Menu > Settings > Account > Two-step verification > Enable. Follow the steps to create a six-digit PIN code that you can easily remember. Importantly, add your email address to retrieve that code in case you forget it. - Disable Cloud Backups. Cloud backups are really important because it keeps a repository of all your old messages, however if you really care about
your privacy, then you should consider disabling your cloud backup. If you back up your WhatsApp messages to iCloud or Google Drive, for example, they’re no longer encrypted and anyone with access to these databases can read all your messages. To disable automatic cloud backups: On iPhone: Go to WhatsApp > Settings > Chats > Chat Backup > Auto Backup > Off
On Android: Go to WhatsApp > Menu > Settings > Chats > Chat Backup > Backup to Google Drive > Never - Protect your privacy on Whatsapp. Control what information other users have access to. You can control who can see your Last Seen, profile
photo, about, status, and live location. You can also turn off Read Receipts here, so the blue check marks are switched off. This depends entirely on what works best for you and for your audience. Go to Settings > Account > Privacy to see everything at your disposal.
The biggest concern with WhatsApp, other than the fact that it doesn’t encrypt its backups, both local and cloud, is the fact that it does not encrypt your metadata which includes for example sender information, recipient information, the dates and times when messages are sent and received, how much information was sent and various data about the devices used. Metadata might seem relatively insignificant, but it can reveal quite a lot about your social networks and about your personal and work-related communication patterns, especially if someone is able to analyse a large volume of it. This is where Signal comes in.
Signal is much better compared to WhatsApp when it comes to security concerns. Other than the features on WhatsApp, Signal also provides:
- Disappearing messages. This feature allows you to set a length of time after which messages to and from a user will disappear. Assuming you want to share the password to a Google Drive containing sensitive information about your students to your colleague, you can send the message to them that’s only visible for 1 hour, after which it disappears. This is an easy way to limit the information that might be exposed if a device is lost, stolen, confiscated or infected with malware. Keep in mind, however, that features like this will not prevent the sender or the recipient of a message from making a copy of it. Wire also has this feature.
- Signal is also able to encrypt metadata. In order to protect user privacy from all corners, Signal devised a new way to communicate between the
sender and the recipient and it’s called Sealed Sender. Basically, with Sealed Sender, no one will be able to know — not even Signal — who is messaging whom, which is amazing. - You can also lock the Signal app with a passcode or biometrics. Additionally there is 2FA and an option to block screenshots within the app and the recent screen. And to top it off, Signal by default encrypts all the local files with a 4-digit passphrase. And if you want to create an encrypted local backup then you can do that as well. All in all, in terms of security and privacy protection, Signal stands head and shoulder above WhatsApp and that makes it the most secure messaging app.
However, before you decide to migrate or enforce any of these options, you should do some research about your audience, what both your needs are, and where they intersect. How do your students normally communicate? What channel is mostly used in your school?
Securing Email Communication
Other than our phones, the most prevalent form of communication in schools and learning institutions is through emails. So how do we ensure that what we share over email is safe and secure? Once again, encryption comes into play. Some educators access their emails through a website such as Gmail, which is very common, while other institutions send and receive using email clients such as Thunderbird, Apple Mail or Outlook. Regardless of how you access your emails, it is important that you employ the use of end-to-end encryption and one of the most well-known forms of end-to-end encryption is called Gnu Privacy Guard (GPG) which can be implemented in emails. PGP which stands for Pretty Good Privacy, is used interchangeably with GPG. As part of the resources, links have been provided on how to use and install PGP in Thunderbird, Outlook, Apple Mail and Gmail as well as some reading for how GPG works.
Some email services already are privacy oriented. Usually, they already have PGP integrated and they are usually affordable and accessible. They include:
- ProtonMail (Web, Android, iOS)
- Tutanota (Web, Android, iOS)
- Posteo (Web)
- Kolab Now (Web)
- mailbox.org (Web)
Securing Other Forms of Online Communication
Other than using emails and communicating via our phones, we log onto school portals, we communicate with friends, family and colleagues over social media, we make transactions online with banking institutions, we buy stuff online, we learn new things by watching videos and entertain ourselves with music and movies online. Most of the time, we access all this information through websites or web applications. While interacting with these sites, how can we confirm that while sharing sensitive information such as student/employee data, banking information, credentials, and even PII, that it is not tampered with while in transit or even in storage?
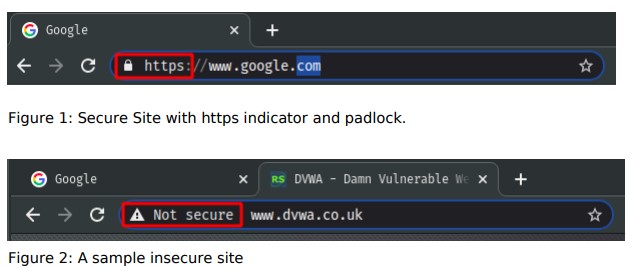
How do we know we are interacting with a secure website?
When you visit a secure website, the Uniform Resource Locator (URL) in your browser’s address bar should begin with HTTPS:// rather than HTTP://: If it does, and if your browser does not display any errors, then you should be communicating through an encrypted connection between your browser and the server where the website is hosted. You may also notice a ‘lock’ symbol near the Web address. These are clues to let you know that it will be much harder for someone to eavesdrop on your communication with that particular website. Some browsers also flag HTTP websites as “not secure.”
You should avoid typing your password, or any other sensitive information, into a website that does not support HTTPS. In addition to passwords and financial transactions, HTTPS also helps protect your webmail messages, search engine queries and social media communication as they travel between you and your provider. If you are using a service like this, and it does not offer you an HTTPS connection, you should switch providers.
If you use Firefox or Chrome as your browser, you can also install the HTTPS Everywhere extension. It will try to ensure that you do not end up using an insecure connection when you visit sites that do support HTTPS.
When it comes to social media communications, employ wisdom and the tried and tested methods we talked about in the CTT course. Just as a recap, ensure that you:
-
- Practise good password hygiene. Use different passwords for your social media accounts, and also make sure each password is complex and unusual. Avoid password re-use. Enable 2FA for all your accounts to prevent unauthorized parties from accessing your accounts. If possible, create a whole new email specifically for social media accounts so that if you are compromised, hackers won’t have access to any valuable information.
- Check what apps are connected to your social media. This usually happens when you use Facebook or Google to sign into other applications. Assess thoroughly if this level of access is necessary.
- Keep your mobile apps and software updated.
- Close the accounts that you’re not using. Forgotten social media accounts may be compromised without being noticed. Hackers can leverage these, and access other accounts linked to it, like your email.
- Limit access to corporate social media accounts to only those who are authorized to have access to them. Additionally, monitor all correspondence that occurs through the corporate social media accounts.