4
In these attacks, a hacker takes advantage of weaknesses present in an application or website to gain access and get data.
Software Application Attack
Threat actors exploit an application installed in a laptop or phone by leveraging the vulnerabilities present. This can result in unauthorized access to privileged information such as a physical address, teacher profiles and student profiles. The following online learning platforms can be affected by a software application attack: Learning Management Systems (LMS), Student Management Systems (SMS) and video conferencing (Zoom, Microsoft Teams, Google Meets, Webex).
Common Software Application Attacks
-
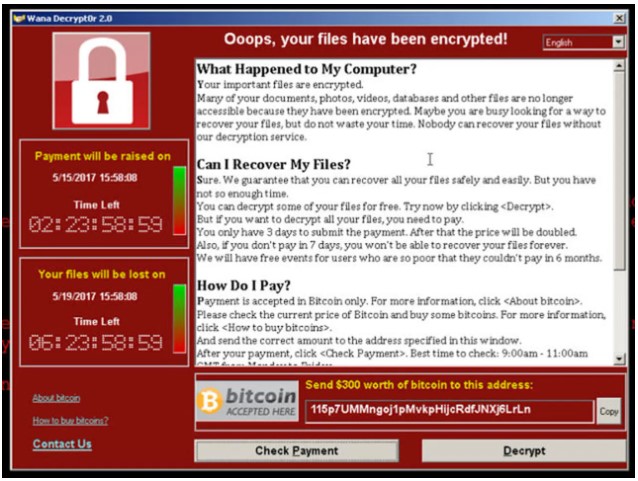
Ransomware
A type of malware that prevents or locks out a user from accessing files, databases or applications and demands for payment mostly in the form of bitcoins. It is designed to spread across a network and target database and file servers, and can quickly cripple an entire organization.
2. Phishing
An attack common in emails where an attacker sends a user an email with a malicious link. Once the user clicks on the link, the threat actor is able to download malware into the computer and affect the school system. This attack can be propagated by using enterprise email clients such as Mozilla Thunderbird, Microsoft Outlook and Mail bird.
An attacker can modify their malicious email addresses inserting terms like ‘principal,’ ‘head of department,’ ‘school,’ and ‘chairperson’ to make them appear legitimate.

3. Brute force attack
A trial and error method used to get sensitive data. An attacker tries to gain access to a system by submitting many guessed passwords and usernames until the correct one is found. It tries to use dictionary passwords which consist of commonly used usernames and passwords.

4. Zero-day attack
A cyber-attack that occurs before vendors can detect or fix the vulnerability. It’s mostly used to target high profile businesses and governments. A vendor or developer can easily fail to detect it hence, very dangerous. An attacker can steal or modify your data and take unauthorized control of the computer.

Web Attack
Humans are considered the weakest link in cybersecurity. Most users are confident that information stored in a trusted website is safe and will be kept private. However, a threat actor can identify loopholes in the website, gain access and read the user’s confidential information. A web attack can affect a school’s website, student and staff portal.
Common Web Attacks
1. Watering Hole Attack
An attacker targets frequently used websites in an organization, for example, school website and install malware that infects user’s devices. The attacker can gain unauthorized access and take over the network.
Video: What is a water hole attack?
2. Drive-by Download Attack
Accidental or unintentional download of malicious code onto a computer or mobile device without your consent, which exposes you to a cyber-attack. A user does not have to click on a link, press download or open a malicious email attachment to become infected.

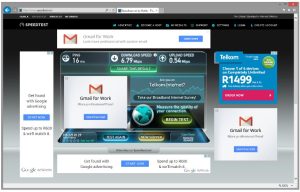
3. Malvertising
An attacker inserts malicious code into a genuine online advert and affects users viewing the webpage. The main aim is to spread malware and compromise systems.
For example, in the image below, an attacker can insert malicious code into Gmail’s advert and host it on a website so that whoever clicks on the advert gets infected. This can happen to a school’s website.
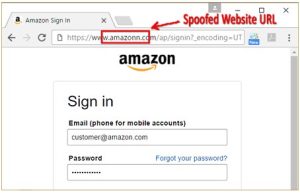
4. Website Spoofing
An attacker creates a fake web site that mimics a legitimate institution’s website, for example, a school portal, with the intention of tricking users and gaining trust. Users may be duped into giving sensitive information, wiring money into a fraudulent account or engaging in activities harmful to the institution.
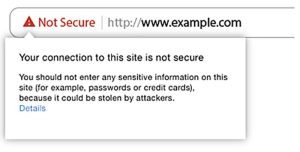
5. Insecure connections
Users should carefully analyze a website link before clicking on it. HTTP (Hypertext Transfer Protocol) is a protocol that enables a user to interact with a website. A website should be secured by using HTTPS (Hypertext Transfer Protocol Secure) instead of HTTP because it adds a layer of security by ensuring safe and private online communication. Kindly check if your school website is secure and if not inform the IT department.
The image below shows an example of an insecure website as it uses HTTP for communication.
Case Studies
1. Zoom bombing attacks disrupt online learning
- https://www.insidehighered.com/news/2020/03/26/zoombombers-disrupt-online-classesracist-pornographic-content
- https://www.the-star.co.ke/news/2020-07-20-intruders-flood-online-classes-with-pornthreats/
- https://www.latimes.com/california/story/2020-10-10/ucla-zoom-bombing-attacks
2. Mount Kenya University Students’ information leaked and posted online. The data consists of names, postal addresses and phone numbers.
3. Ethical hackers break into several universities’ networks in two hours. They mostly used phishing emails to execute the attack.
4. A bored teen hacked into blackboard, an online learning platform used by his school and found bugs that exposed student data.
5. Learnaholic, an IT vendor in Singapore fined $60,000 after more than 47,000 personal data of students, parents and staff of various schools were hacked.
6. A hacker released confidential information after the school district refused to pay a ransom.
Countermeasures
- Patch and update your software applications. Companies such as Microsoft often send patches on Windows 10 when a vulnerability is discovered.
- Scan for any malware in your device using anti-malware, anti-virus or anti-spyware
- Ensure the websites you visit are secure. Do not accept anything over HTTP connections
- Use safe browsing tools provided by various antivirus vendors such as AVG Secure Browser
- Use two-factor authentication tools to prevent unauthorized access. An example is Google Authenticator used for validating a user before accessing a Gmail account.


