2
Introduction
The main purpose of cybersecurity is to ensure Confidentiality, Integrity and Availability (CIA) of data and services. The CIA triad is a model that is used to secure information. The CIA triad is essential in cybersecurity as it provides important security considerations to safeguard and protect critical information. In this article, you will learn how the CIA triad enhances your security.
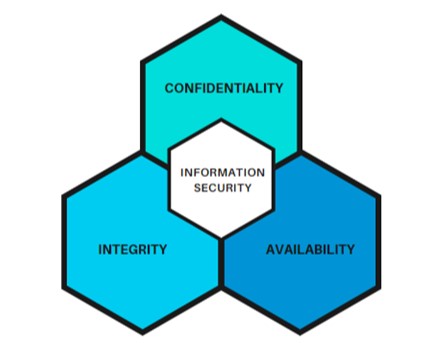
What is Confidentiality?
Confidentiality refers to efforts to keep data private or secret. Confidentiality ensures that information is accessed only by authorized personnel. For example, access to the student management system should be granted to teachers and denied for non-teaching staff. Unauthorized personnel should not be allowed to access any sensitive data as this could lead to privacy issues and data breaches. A data breach is a security incident that exposes confidential or protected information to the public or to unauthorized parties.
Confidentiality is achieved through effective identification and authentication. This can be done through the use of usernames, passwords, biometrics (e.g. fingerprints) and identification (ID) badges. For confidential files, you can maintain confidentiality by password-protecting the files so that, anyone without the password cannot access the files.
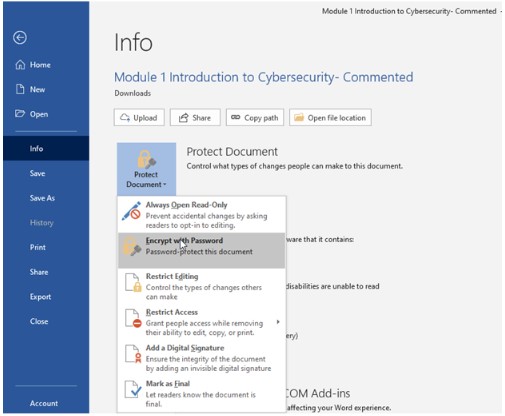
On Windows you can do this using the following steps:
- Go to File > Info > Protect Document > Encrypt with Password.
- Type a password, then type it again to confirm it.
- Save the file to make sure the password takes effect.
Confidentiality examples:
- Accessing your laptop or phone using a fingerprint, PIN or a password known only to you.
- Sending emails over a secure communication channel
- Using secure messaging platforms such as WhatsApp and Telegram
- Showing your ID badge to the security personnel at the school gate before being let in.
- Using a password to access your email account.
- Using a password to protect a folder containing your students’ exam results.
What is Integrity?
Integrity is about ensuring that data has not been tampered with. Therefore, integrity prevents unauthorized modification or deletion of data. Only authorized personnel should be allowed to make changes or delete data. It ensures that the data is correct, authentic, and reliable. Data must be protected while in use, in transit, and when stored.
Integrity examples:
- Teachers can only change the grades of the subjects that they teach.
- Students should not be allowed to change their grades.
- Limit access to files because if unauthorized people cannot access the documents, they cannot tamper with them. This can be done by password protecting your devices and documents.
- Maintain backup copies of confidential data to ensure you have a clean copy to revert to in case of any tampering.
- Use secure communication channels to send and share data to prevent it from being intercepted and tampered with.
What is Availability?
Availability refers to the guarantee of reliable and timely access to information and services by authorized people. This ensures that authorized personnel can access networks, systems, applications and information whenever needed.
Examples of availability:
- Teachers can access the school’s student management system any time.
- A good internet connection will ensure availability when accessing information online
- Students can access their results in a timely manner.
- Students can access the learning management systems at their convenience.
Confidentiality, integrity, and availability can all be easily tampered with by cyber-attacks leading to loss and modification of information. When implementing security measures, consider what element of the CIA triad each measure attempts to protect and maintain. For example, implementing a fingerprint lock on your mobile phone protects your information’s confidentiality and integrity.

